AI Primer Series | the New Cybersecurity Threat

In today's rapidly evolving digital landscape, artificial intelligence has fundamentally altered the cybersecurity equation. What was once sufficient protection is now dangerously inadequate against increasingly sophisticated threats. This shift demands not just awareness, but a complete rethinking of our security practices.
The AI Advantage for Attackers
Cybercriminals are using artificial intelligence to execute more dangerous and convincing phishing attacks. According to a 2024 study commissioned by Keeper Security, IT leaders are witnessing AI-powered attacks increase at a rate of 51% and identify AI-powered attacks as the most serious emerging threat facing their organizations.
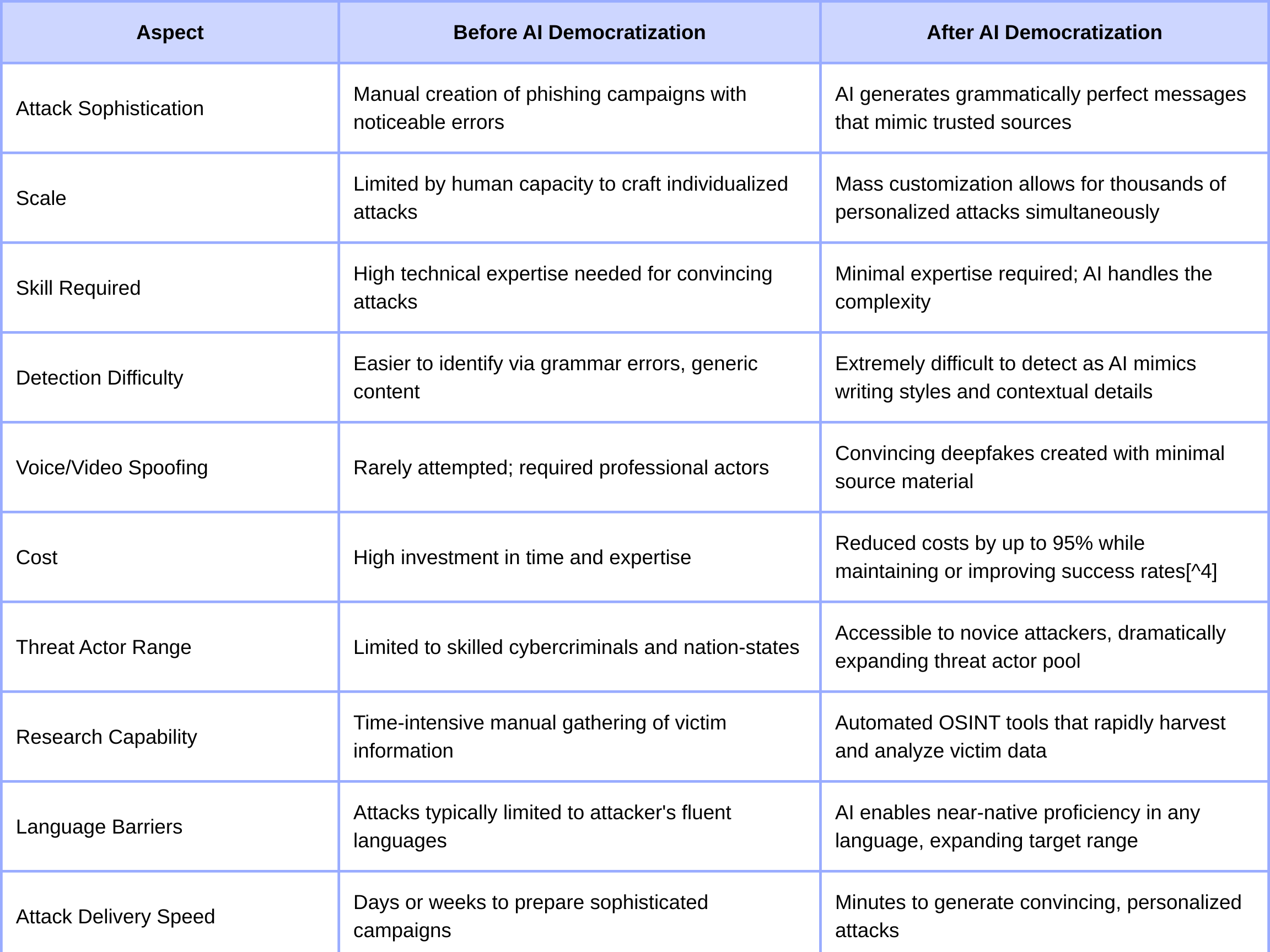
The democratization of advanced hacking capabilities represents the most concerning development in cybersecurity today. What once required years of specialized knowledge can now be accomplished by individuals with minimal technical expertise but access to AI tools.
Writing More Convincing Phishing Messages
Generative AI tools like ChatGPT allow threat actors to craft phishing messages without the typical telltale signs that previously helped users identify scams. These AI-generated messages contain no grammatical or spelling mistakes, incorporate urgent language, and include convincing pretexts that make traditional detection methods ineffective. Recent research has shown that AI-generated phishing messages have demonstrated a 54% click-through rate, compared to 12% for human-written messages.
Advanced Social Engineering
AI significantly enhances social engineering capabilities by enabling cybercriminals to research their targets more efficiently. In May 2024, the FBI issued an advisory warning about the increased use of AI and deepfake technology to spoof audio and video for calls, messages, and voicemails. These tools allow attackers to process and synthesize information about potential victims without spending hours on laborious research, making their social engineering attacks far more convincing.
Social Engineering: Before vs. After AI Democratization
Voice and Identity Impersonation
Perhaps most alarmingly, cybercriminals are now using AI to mimic how people typically write their emails or texts, and can even use AI to impersonate people's voices. AI can generate convincing visual content, including deepfake photos or videos, to impersonate trusted contacts. According to cybersecurity experts, modern voice cloning technology requires as little as three seconds of audio to create a convincing replica of someone's voice.
Social Media: A Goldmine for AI-Powered Attacks
Today's AI-powered attack tools are particularly dangerous because of how efficiently they can scrape and analyze content from social media profiles. Modern OSINT (Open Source Intelligence) tools can automatically harvest vast amounts of personal data from public profiles across platforms like LinkedIn, Facebook, Twitter, and Instagram.
These tools can collect:
- Personal details (birthdays, locations, family relationships)
- Professional information (work history, colleagues, organizational structures)
- Writing samples (for voice and text style mimicry)
- Voice clips from posted videos (for voice cloning)
- Photos (for generating deepfakes or analyzing home security)
- Regular behavioral patterns (when you're at work, on vacation, etc.)
The information gathered is then processed by AI systems that can identify the most effective social engineering angles. For example, if your profile shows you recently started a new job, attackers might impersonate your new boss with an urgent request, knowing you're less likely to question authority in a new role.
Recommendation: Consider making your social media profiles private or significantly limiting the personal information you share publicly. Regularly review your privacy settings across all platforms, as these often change without notice. Be particularly cautious about posting voice recordings, videos of yourself speaking, or details about your work hierarchy that could be exploited.
Real-World AI Attack Examples
Deepfake Financial Fraud at Arup
In one of the most significant cases of AI-enabled fraud to date, engineering firm Arup lost $25 million when fraudsters used deepfake technology to impersonate the company's chief financial officer and other executives in a video conference call with a finance employee at their Hong Kong office in early 2024. The employee had initially been suspicious of an email requesting a secret transaction, but the deepfake video call was so convincing that they proceeded to transfer the funds.
Voice Cloning Family Emergency Scam
In January 2023, Arizona mother Jennifer DeStefano received a call in which she heard what sounded exactly like her 15-year-old daughter's voice crying and saying, "Mom, these bad men have me. Help me." A man then demanded a ransom payment. The voice was actually an AI-generated clone of her daughter's voice, who was safely away on a ski trip at the time. The scammer initially demanded $1 million before attempting to negotiate a lower amount.
AI-Powered Corporate Phishing Campaigns
According to a 2024 report from Help Net Security, file-sharing phishing volume increased by 350% between June 2023 and June 2024, with 60% of these attacks exploiting legitimate domains such as Gmail, iCloud, Outlook, and collaboration platforms. These sophisticated attacks use generative AI to craft highly convincing communications that eliminate spelling and grammatical mistakes while creating realistic-looking phishing pages.
Understanding Zero-Click Attacks
Zero-click attacks represent one of the most sophisticated threats in today's cybersecurity landscape. Unlike traditional cyberattacks that require user interaction (such as clicking a malicious link), zero-click exploits require no action from the victim to compromise their device.
How Zero-Click Attacks Work
These attacks exploit vulnerabilities in how data gets processed on your device. They can arrive through hidden text messages, emails, voicemails, or image files delivered via Wi-Fi, NFC, Bluetooth, or other communication channels. Once received, they automatically activate an unknown vulnerability in your device's hardware or software without any warning signs or user interaction.
According to recent security reports, zero-click attacks have seen a troubling surge in 2024, with a particular focus on mobile devices and social media platforms. These attacks are especially dangerous because they leave minimal traces, making them difficult to detect until damage has already occurred.
Protecting Against Zero-Click Threats
While zero-click attacks are challenging to defend against, you can implement several proactive measures:
- Keep all software updated: Regularly update your operating system, applications, and firmware to patch known vulnerabilities that zero-click exploits might target.
- Install security solutions with behavioral analysis: Advanced endpoint protection solutions can detect unusual system behaviors that might indicate a zero-click attack in progress.
- Limit app installations: Only download applications from official stores and regularly delete apps you no longer use, especially messaging or communication apps that process data from untrusted sources.
- Enable automatic updates: Make sure critical security patches are applied as soon as they're available.
- Consider periodic device restarts: The NSA has suggested that restarting your mobile device weekly can sometimes prevent certain types of zero-click attacks from persisting, though this isn't foolproof.
- Implement Remote Browser Isolation (RBI): For organizations, this technology can provide a secure environment separated from the underlying host system.
VPNs: Understanding Their Role and Limitations
Virtual Private Networks (VPNs) are frequently promoted as essential security tools, but it's crucial to understand exactly what they can and cannot protect against.
What VPNs Do Protect Against
VPNs create an encrypted tunnel for your internet traffic, which provides several important protections:
- ISP Monitoring: VPNs prevent your Internet Service Provider from seeing your browsing activity.
- Public Wi-Fi Risks: When using public networks, VPNs encrypt your data, protecting it from potential eavesdroppers.
- IP Address Exposure: VPNs mask your real IP address, making it more difficult for websites to track your location or identify your specific device.
- Some Geographic Restrictions: VPNs can help bypass certain region-based content limitations.
What VPNs Do NOT Protect Against
Despite their benefits, VPNs have significant limitations:
- Malware and Phishing: VPNs do not scan for or block malicious software or phishing attempts. They encrypt your connection but cannot prevent you from downloading malware or entering credentials on fake websites.
- Browser Fingerprinting: Websites can still identify you through browser fingerprinting techniques that don't rely on your IP address.
- Cookies and Trackers: VPNs don't block cookies or prevent websites from tracking your activity once you're on their site.
- Weak Passwords: VPNs provide no protection against compromised credentials or poor password practices.
- Data Breaches: If a service you use experiences a data breach, your information can still be exposed regardless of VPN use.
- Zero-Day Vulnerabilities: VPNs themselves can contain security flaws. In 2024, several major VPN providers experienced significant vulnerabilities that put users at risk.
For comprehensive protection, combine VPN usage with strong passwords, multi-factor authentication, updated software, and robust antivirus/anti-malware solutions. Remember that a VPN is just one component of a complete security strategy, not a complete solution on its own.
The Link Hover Method: Your First Line of Defense
One of the simplest yet most effective security practices is verifying links before clicking on them. This technique, known as the "hover method," can help you identify and avoid malicious links that might otherwise lead to credential theft, malware installation, or other attacks.
How to Use the Hover Method
- Desktop Browsers: Position your cursor over any link without clicking. Most browsers will display the actual destination URL in the bottom-left corner of your window.
- Mobile Devices: On smartphones and tablets, you can typically press and hold a link (without tapping) to see a preview of the URL.
What to Look For
When examining a link, pay attention to these critical elements:
- Domain Name: Focus on the "root domain" (what appears between "https://" and the first "/"). For example, in "https://www.example.com/page", "example.com" is the root domain. Phishing sites often use similar-looking but slightly altered domains like "examp1e.com" or "example-secure.com".
- HTTPS: Legitimate sites should use secure HTTPS connections (indicated by a padlock icon), though be aware that phishing sites can also use HTTPS.
- Suspicious Additions: Be wary of domains with unusual prefixes or suffixes, such as "secure-paypal.randomdomain.com" – the actual domain here is "randomdomain.com", not PayPal.
- URL Shorteners: Links masked by URL shortening services (like bit.ly or tinyurl) hide the actual destination. Consider using URL expander tools to see where these lead before clicking.
Recent data shows web threats increased by approximately 17% from late 2023 to mid-2024, making this simple verification technique more important than ever.
Adopting a Zero Trust Mindset
In today's complex threat landscape, the traditional security perimeter has disappeared. The zero trust model operates on the principle of "never trust, always verify" – treating every user, device, and connection as potentially compromised until proven otherwise.
Core Principles of Zero Trust
- Verify Explicitly: Authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use Least Privileged Access: Limit user access with just-in-time and just-enough access (JIT/JEA), risk-based adaptive policies, and data protection.
- Assume Breach: Minimize blast radius for breaches and prevent lateral movement by segmenting access by network, user, devices, and application awareness. Verify all sessions are encrypted end to end. Use analytics to get visibility, drive threat detection, and improve defenses.
Implementing Zero Trust in Your Personal Security
While zero trust is often discussed in organizational contexts, individuals can adopt similar principles:
- Question Every Request: Whether it's an email asking for information, a call requesting action, or a website seeking credentials, verify through secondary channels before proceeding.
- Limit Access by Default: Use separate accounts for different purposes, and avoid giving applications or services more permissions than absolutely necessary.
- Verify Before Acting: Confirm unusual requests directly with the purported sender via a different communication method.
- Segment Your Digital Life: Use different email addresses and even devices for sensitive activities versus casual browsing.
Password Managers: Beyond Basic Security
A robust password manager is essential for managing today's complex digital identities. Bitwarden stands out as a particularly strong option due to its combination of security features, cross-platform compatibility, and affordability.
Why Choose Bitwarden
Bitwarden offers several advantages that make it an excellent choice for password management:
- Open-Source Security: As an open-source solution, Bitwarden's code undergoes constant scrutiny from security experts worldwide. Bitwarden's open-source nature is crucial for security because it enables thousands of independent experts to inspect the code for vulnerabilities, ensuring transparency and rapid identification of potential security flaws. This "many eyes" approach provides verifiable security rather than requiring blind trust in the vendor's claims, which is especially important for a tool safeguarding your most sensitive credentials.
- Cross-Platform Compatibility: Bitwarden works across virtually all platforms and browsers, including Chrome, Firefox, Safari, Edge, Brave, Vivaldi, Opera, and Tor Browser, as well as Windows, macOS, Linux, iOS, and Android.
- Strong MFA Support: Bitwarden supports multiple forms of multi-factor authentication, including authentication apps (TOTP), email verification, YubiKey, FIDO2 WebAuthn, and Duo Security.
- Browser Independence: Unlike browser-built-in password managers, Bitwarden doesn't tie you to a specific browser ecosystem, providing more flexibility and security.
- Free Tier Availability: Bitwarden offers a robust free version that includes unlimited passwords, device syncing, and basic 2FA.
Setting Up MFA with Bitwarden
For optimal security, enable multi-factor authentication on your Bitwarden account:
- Log into your Bitwarden web vault
- Go to Account Settings → Two-step Login
- Choose your preferred authentication method (authenticator app recommended)
- Follow the setup instructions to link your authenticator app or security key
- Save your recovery codes in a secure, offline location
Remember that a password manager with MFA enabled provides significantly better protection than memorized passwords or browser-based password storage.
Browser Security: Choosing the Right Defense
Your choice of web browser plays a significant role in your overall security posture. Each major browser offers different security features and philosophies.
Browser Security Comparison
Firefox
- Privacy-focused with built-in tracking protection
- More security-oriented than Chrome with regular updates
- Offers a master password feature to protect saved credentials
- Allows extensive customization through security-enhancing add-ons
- Non-profit backed with transparent privacy policies
Brave
- Built with privacy as a primary focus
- Blocks ads and trackers by default
- Includes HTTPS Everywhere functionality
- Offers Tor integration in private windows
- Chromium-based but removes Google's tracking components
Chrome
- Regular security updates and sandboxing for tab isolation
- Google's Safe Browsing API protects against malicious sites
- Strong site isolation features
- Less privacy-focused than alternatives (collects more user data)
- Excellent extension ecosystem but requires careful vetting
Edge
- Microsoft Defender SmartScreen offers malware protection
- Tracking prevention features included
- Password Monitor checks for compromised credentials
- Chromium-based with Microsoft's security additions
- Integrates with Windows security features
For maximum security, consider these browser practices regardless of your choice:
- Keep Your Browser Updated: Always install the latest updates as they often contain critical security patches.
- Use Privacy-Enhancing Extensions: Consider reputable extensions like uBlock Origin for ad blocking and privacy protection.
- Disable Unnecessary Features: Turn off features you don't use, particularly those that might expose data like location services or notification permissions.
- Regular Extension Audits: Periodically review and remove extensions you no longer use or trust.
- Use Separate Browsers: Consider using different browsers for different activities – one for banking and sensitive tasks, another for general browsing.
The SHIELD Framework: A Practical Approach to AI-Era Cybersecurity
After understanding the various threats and defensive measures discussed in this article, you may be wondering how to prioritize and implement these security practices in your daily life or business. The SHIELD Framework provides a structured approach to assessing and enhancing your cybersecurity posture in the age of AI-powered threats.

S: Situational Awareness
Begin by understanding your specific threat landscape. Different individuals and organizations face different risks based on their digital footprint, industry, and online behaviors.
Key Actions:
- Conduct a personal or organizational "attack surface" inventory (what accounts, devices, and data do you have exposed?)
- Identify your most valuable digital assets (financial information, intellectual property, personal identity data)
- Consider which AI-powered threats are most relevant to your situation (Are you more vulnerable to voice cloning? Deepfakes? Phishing?)
H: Hardening Fundamentals
Before implementing advanced security measures, ensure you've covered the essential cybersecurity basics. These fundamentals provide a strong foundation for more sophisticated defenses.
Key Actions:
- Enable multi-factor authentication on all critical accounts
- Use a reputable password manager like Bitwarden
- Keep all software and operating systems updated
- Backup critical data following the 3-2-1 rule (3 copies, 2 different media types, 1 off-site)
- Encrypt sensitive information and communications
I: Identify Vulnerabilities
Regularly assess your digital presence for potential weaknesses that could be exploited by AI-enhanced attacks.
Key Actions:
- Conduct periodic security audits of your devices and accounts
- Review privacy settings across all social media platforms
- Use haveibeenpwned.com to check if your credentials have been compromised
- Evaluate third-party services and vendors for security risks
- Consider professional vulnerability assessments for businesses
E: Evaluate AI Risks
As AI capabilities continue to evolve, stay informed about new threat vectors and adjust your security practices accordingly.
Key Actions:
- Follow cybersecurity news sources to stay current on AI-enabled threats
- Consider how voice samples, photos, or writing patterns you share online could be exploited
- Evaluate which AI security tools might benefit your specific situation
- Develop protocols for verifying unusual requests that might be AI-generated
L: Layered Protection
Don't rely on a single security solution. Implement multiple defensive measures so that if one fails, others are still in place to protect you.
Key Actions:
- Combine technical solutions (VPNs, antivirus, firewalls) with behavioral practices
- Segment your digital life with different accounts for different purposes
- Use browser extensions that enhance security (like ad blockers and tracker blockers)
- Implement network-level protection in addition to device-level security
- Maintain separate devices for highly sensitive activities (when feasible)
D: Decision Verification
Apply zero trust principles to your digital interactions, verifying unusual requests through secondary channels before taking action.
Key Actions:
- Establish verification procedures for financial transactions or data transfers
- Create authentication codes or "safe words" for family and close colleagues
- Always hover over links before clicking to verify destinations
- Confirm unexpected requests via a different communication method
- Question urgent demands for action, especially those involving credentials or money
By applying the SHIELD Framework systematically, you can develop a more resilient security posture that addresses both current and emerging AI-enhanced threats. Remember that cybersecurity is not a one-time project but an ongoing process that requires regular attention and updates as the threat landscape evolves.
Why Everyone Is a Target: The New Reality of Cyber Threats
If you've read this far and thought, "This is interesting, but surely I'm too small a target," think again. The uncomfortable truth of today's cybersecurity landscape is that no one is too insignificant to be targeted. In fact, being "small" often makes you a more attractive target.
Small Businesses: Prime Targets in the AI Era
Recent data paints a sobering picture: 46% of all digital breaches target businesses with fewer than 1,000 employees, and a staggering 61% of all cyberattacks specifically aim at small to medium-sized businesses. What's more troubling is that 59% of small business owners without cybersecurity measures believe their company is "too minuscule to be targeted"—precisely the misconception that makes them vulnerable.
The economics of cybercrime have changed dramatically with AI tools. Attackers no longer need to focus exclusively on large enterprises for substantial payoffs. Instead, they can efficiently target hundreds or thousands of smaller businesses simultaneously, with minimal investment of time or resources. The attack automation capabilities of AI mean that cybercriminals can cast wider nets with greater precision.
Consider this: in the third quarter of 2024 alone, organizations worldwide experienced an average of 1,876 cyberattacks each—a 75% increase from the same period in 2023. This isn't happening just to Fortune 500 companies; it's happening to local accounting firms, independent medical practices, regional retailers, and family-owned manufacturing companies.
Individuals: Personal Exploitation at Scale
For individuals, the threat is equally pressing. One in ten adults globally has already experienced an AI voice scam, and among those who fell victim, 77% lost money. These aren't random attempts—they're highly targeted attacks using information scraped from your digital footprint.
The data you share online—your vacation photos, voice clips in videos, work announcements on LinkedIn—all provide the raw materials AI needs to create convincing impersonations. Remember: for voice cloning, attackers need just three seconds of audio. For deepfakes, a few clear photos will suffice. Nearly everyone has shared at least this much online.
The Democratization of Cybercrime
Perhaps most alarming is how AI has democratized cybercrime. What once required advanced technical skills and significant resources is now accessible to virtually anyone. Malicious AI tools are readily available on the dark web, complete with user-friendly interfaces and even customer support. Some operate on subscription models, offering "cybercrime-as-a-service" to anyone with basic computer literacy and a few hundred dollars.
In late 2024, cybersecurity experts observed a 40% increase in AI-driven attack campaigns launched by individuals with no prior hacking experience.[^23] These weren't sophisticated attacks—but they didn't need to be. With AI handling the technical aspects, even rudimentary attempts can succeed at scale.
The Cost of Complacency
The financial impact of these attacks can be devastating. For small businesses, the average cost of a data breach ranges from $826 to over $650,000, with many unable to recover and closing within six months of an incident.[^24] For individuals, the costs extend beyond financial losses to include stolen identities, damaged credit histories, and compromised personal data that can be exploited for years.
But perhaps the greatest danger today is complacency—the persistent belief that "it won't happen to me." This mindset is precisely what modern attackers count on. By the time most victims realize they're being targeted, it's often too late.
Taking Action Now
The good news is that implementing even basic security measures puts you ahead of many potential targets. Cybercriminals, like any predators, typically pursue the path of least resistance. By following the recommendations in this article—enabling MFA, using a password manager, verifying links before clicking, maintaining software updates, and adopting a zero-trust mindset—you significantly raise the bar for attackers.
Remember: In today's threat landscape, security isn't optional; it's essential. You don't need to be a high-value target to be targeted—you just need to be connected. And in our interconnected world, that includes virtually everyone.
The question isn't whether you'll face these threats, but how prepared you'll be when you do.

Member discussion